- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Hunting for a Sliver in a haystack
In this blog post, we’ll delve into methods to detect the Sliver framework and explore how to hunt for threat actors – such as APT29[1], also known as Cozy Bear – who have leveraged the Sliver framework to achieve their objectives.
Sliver is a command-and-control (C2) framework which has the capabilities to covertly manage and control remote systems, using reliable communication channels with targeted systems. This enables information gathering and the execution of various post-exploitation activities. In the past, the framework has been weaponized by APT29 and several ransomware groups[2].
Introduction
The Sliver framework[3] was published in 2019 by Bishop Fox as an open-source, cross-platform adversary emulation framework. The framework is written in Golang which supports cross-compilation across Windows, Unix and MacOS. The framework is designed as an open-source alternative for Cobalt Strike, an adversary simulation tool used by numerous advanced persistent threats (APTs) and ransomware groups[4]. Defences for Cobalt Strike have improved over the years due to the popularity of the framework - thus, Sliver is an alternative for threat actors looking for lesser-known toolset by defenders - for now.
In addition, Sliver provides an alternative to other C2 frameworks, due to its convenient modular system of payloads made with Armory[5], an alias and extension package manager of Sliver. This can be used to install various third-party tools such as beacon object files (BOFs) and .NET tools such as Rubeus, SharpMapExec, SharpRDP and SharpHound. BOF is a compiled C program that can be executed within a beacon process and can be leveraged to extend C2 frameworks with post-exploitation features.
Sliver can be deployed on a single server, has a client-server architecture and is designed as a stage-two payload using implants, supporting beacon mode and session mode. Beacon mode implements asynchronous communication, where the implant periodically checks in with the server to retrieve and execute tasks. Whereas session mode will create a real-time session using a persistent connection or by long polling, which is a push-based approach that allows the server to respond to the client when needed.
The term stage[6] denotes the designated goal of the phase of an attack, which can be used by red teamers and threat actors to determine what tools will be used to achieve that goal:
- Stage-zero focuses on achieving initial access to an environment, facilitated by malware like Qakbot, IcedID, Emotet and Trickbot;
- Stage-one involves maintaining persistence access within an environment, utilizing tools such as Cobalt Strike and various remote management tools;
- Stage-two involves executing privilege escalation and lateral movement techniques, which is what Sliver can be used for;
- Stage-three encompasses the usage of tools aimed at locating and extracting data from an environment, with tools such as MEGASync, Rclone and various remote management tools.
Leveraging Velociraptor to detect Sliver attack methods
The Sliver framework is open source and available on Github, and at the time of writing has 82 contributors. By reading the source–code, three Sliver attack methods could be identified for analysis. These methods have been mapped to the MITRE ATT&CK framework[7] alongside the data sources that can be leveraged to detect the execution of these methods, as shown in Table 1.
|
Technique ID |
Description |
Data source ID |
Description |
|
T1059.001 |
Sliver can execute Powershell. |
DS0009 |
Monitor for newly executed Powershell processes. |
|
T1134.001 |
Sliver has the ability to manipulate user tokens. |
DS0009 |
Monitor for running processes and threads with impersonated tokens. |
|
T1055 |
Sliver can inject shellcode into processes. |
DS0009 |
Monitor for the execution of process injection techniques. |
Table 1 - Sliver attack methods mapped to the MITRE ATT&CK framework
The following sub-paragraphs describe how these methods can be detected with Velociraptor, an open-source digital forensics tool which can be used to actively hunt and monitor systems for suspicious activity. The aforementioned artefacts can be found on the Velociraptor documentation page.
1. Detecting a remote shell
Sliver can be used to start PowerShell on a Windows system using the command shell. PowerShell is an interactive command-line interface and scripting environment designed for the Windows operating system. PowerShell was one of the most popular techniques used by threat actors between 2020 and 2022 [8], as observed by Mandiant, Red Canary, MITRE and the Cybersecurity and Infrastructure Security Agency (CISA) of the United States.
Depending on how PowerShell is executed on a Windows system, it leaves behind traces in the Windows Registry (execution policy), Windows event log, and in the memory of the system. Sliver’s built-in command shell executes PowerShell commands with the executable C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe and the process argument -NoExit[Console]::OutputEncoding=[Text.UTF8Encoding]::UTF8
By utilizing Velociraptor on the targeted system, this attack method can be detected using the following Velociraptor artefacts:
- The artefacts
Generic.System.PstreeandWindows.Forensics.ProcessInfoby hunting for processes of which Powershell is a child-process; - The artefacts
Generic.System.PstreeandWindows.Forensics.ProcessInfoby hunting for the specific executable and process argument used by Sliver; - The artefacts
Windows.EventLogs.PowershellModuleandWindows.System.Powershell.PSReadlineto hunt for malicious commands that were executed by Sliver; - In addition, the artefact
Windows.ETW.Powershellcan be used to detect script blocks and commands load monitoring using the Windows Event Tracing (ETW) providerMicrosoft-Windows-PowerShell.
2. Escalate privileges by stealing tokens
The Windows operating system uses tokens to determine the ownership of processes. These tokens can be used to gain higher-level permissions by elevating the security context of processes. Sliver can steal a token of a targeted user account and use it to start an elevated Command Prompt with the command impersonate. By iterating over all running processes and by reading the token of a process (OpenProcessToken), which is owned by the targeted user account to impersonate (ImpersonateLoggedOnUser) the user and the duplicate token (DuplicateTokenEx). After which, the necessary privileges (SeAssignPrimaryTokenPrivilege and SeIncreaseQuotaPrivilege) are enabled (AdjustTokenPrivileges) for the current thread of the Command Prompt.
The thread that uses the stolen token within the process of the Command Prompt can be detected with the Velociraptor artefact Windows.Detection.Impersonation. As shown in Figure 1, the token of the thread is owned by the user account ‘NT AUTHORITY\SYSTEM’ (ImpersonationToken.User) which does not have the same owner as the token of the process in which it is executed - that is owned by the user account ‘MSEDGEWIN10\IEUser’ (OwnerSid). At the time of writing the command impersonate of Sliver does not work[9], but the end result is the same when impersonating a user account with the Windows exploitation tool Mimikatz.
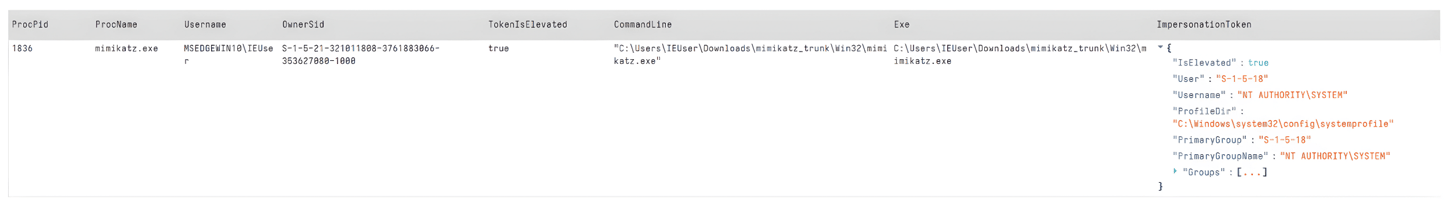
Figure 1 – Thread with an impersonated token detected by the Velociraptor artefact Windows.Detection.Impersonation
3. Conceal the execution of code by injecting shellcode into processes
The concealing of code execution helps to evade detection from security solutions that perform process-based defences, by injecting malicious code in the memory region of a separate process. Sliver can inject shellcode into processes and execute it using the command execute-shellcode.
By default, Sliver does this by executing the executable C:\windows\system32\notepad.exe and creating (VirtualAllocEx) a memory region in the process with read and write access (PAGE_READWRITE), after which the shellcode is written (WriteProcessMemory) into the region. The region is then adjusted to execute and read-only access (PAGE_EXECUTE_READ), which allows the shellcode to be executed by creating a thread (CreateRemoteThread).
As explained in our blog post titled ‘Concealed Code Execution: Techniques and Detection‘, using the Windows system monitor (Sysmon) is the most convenient option to detect concealed code execution. Sysmon[10] is a Windows system service and device driver executions and network connections. The explained process injection method by Sliver results in the Sysmon events shown in Table 2 provider Microsoft-Windows-Sysmon/Operational.
|
Sliver |
Sysmon event |
|
Sliver implant is executed. |
Event ID 1: Process creation |
|
Sliver creates a child-process. |
Event ID 1: Process creation |
|
Sliver opens the process. |
Event ID 10: ProcessAccess (the logging of this event could cause high system load) |
|
Sliver writes the shellcode to a memory region in the process. |
This is a blind spot because Sysmon does not monitor read and write memory events. |
|
The remote thread is created to execute the shellcode. |
Event ID 8: CreateRemoteThread |
Table 2 – Sliver shellcode execution and the Sysmon events it leaves behind
By Installing Sysmon with the Velociraptor artefact Windows.Sysinternals.SysmonInstall and the configuration from SwiftOnSecurity[11], these events can be monitored for process injection behaviour using the Velociraptor Query Language (VQL) with the following query:
|
LET events = SELECT * FROM parse_evtx(filename="C:\\Windows\\System32\\WinEvt\\Logs\\Microsoft-Windows-Sysmon%4Operational.evtx") WHERE System.EventID.Value IN (1, 8) LET processes = SELECT EventData.ProcessId AS ProcessId FROM events WHERE System.EventID.Value = 1 LET child_processes = SELECT EventData.ProcessId AS ProcessId FROM foreach( row=processes, query={ SELECT * FROM events WHERE System.EventID.Value = 1 AND EventData.ParentProcessId = ProcessId }) LET remote_threads = SELECT *FROM foreach( row=child_processes, query={ SELECT * FROM events WHERE System.EventID.Value = 8 AND EventData.TargetProcessId = ProcessId }) SELECT * FROM remote_threads |
In addition, the detected processes can be scanned with Yara[12] and dumped (proc_dump) for further analysis. This approach enables us to perform memory forensics on thousands of systems in a scalable manner, without the need to acquire full memory images of all systems.
Combining Endpoint Detection & Response solutions with Velociraptor
The data source processes (DS0009) located in the memory of a system, as shown in Table 1, is the most important data source to detect the three analysed attack methods of Sliver. This also applies to most of the other attack methods that Sliver has. Velociraptor heavily depends on the use of basic memory forensics and Yara to detect these methods, whereas modern endpoint detection & response (EDR) solutions have built-in detection capabilities that leverage Event Tracing for Windows (ETW) for methods that leave traces in memory. Because of that, the use of an EDR is vital to detect Sliver. Additionally, Velociraptor serves as a valuable complement to an EDR by providing threat hunting and remediation capabilities that an EDR might not have, to respond to threat actors leveraging Sliver.
Detecting network protocols used by Sliver
Sliver implants need to communicate with a Sliver C2 server so that threat actors can remotely execute these attack methods on the targeted systems. The network protocols HTTP (default), HTTPS, DNS, mutual TLS (mTLS) and Wireguard are supported by Sliver. Depending on the environment a widely used protocol might decrease the chance of detecting an implant based on network traffic.
Of all these protocols, Sliver recommends mTLS, a protocol that uses mutual authentication and ensures that both the client and the server are who they claim to be based on TLS certificates. This provides an additional layer of security, because an unauthorized client can’t just send a request to C2 servers. This does not mean that these C2 servers can’t be tracked on the internet, it just means it’s a little more tricky. Due to the use of TLS, the TLS configuration can be fingerprinted with JARM[13], a network fingerprinting tool that enables the identification of C2 servers based on the TLS configuration.
JARM was released in 2020 and supports the fingerprinting of an active server that uses TLS, by connecting with the server and capturing specific attributes of the TLS server responses, which are hashed to produce a JARM fingerprint. This fingeprint can then be used to hunt for C2 servers using network security solutions like Shodan and Censys.
The use of techniques to communicate with targeted systems to control them belongs to the tactic command and control as part of the MITRE ATT&CK framework[14]. Table 3 provides an overview of the C2 communication methods of Sliver mapped to the corresponding technique and the detection methods that can be leveraged to detect C2 network traffic initiated by Sliver in an environment.
|
Protocol |
Technique ID | Detection method |
| TCP | T1071.001 |
|
| DNS | T1071.004 |
|
| mTLS | T1573.002 |
|
| WireGuard | T1572 |
|
Table 3 - Detection methods for network protocols used by Sliver
Conclusion
In this blog, we have examined why the Sliver framework has gained traction among threat actors and why it currently stands as a viable alternative to Cobalt Strike. We then explored three key attack methods employed by Sliver, and how Velociraptor can be used to detect these methods in real-time. This was done by hunting for traces left behind in the following data sources: memory, filesystem and the Windows event log using System Monitor (Sysmon) for Windows. Of these data sources, the memory of a system was proven to be the most important data source for most of the attack methods of Sliver.
Luckily, modern endpoint detection & response solutions (EDR) have such built-in detection capabilities, which leverage Event Tracing for Windows (ETW) to detect methods that leave traces in memory. This demonstrates the essential role of a properly configured EDR to enable detection of Sliver. Additionally, Velociraptor serves as a valuable complement to an EDR by providing threat hunting and remediation capabilities that an EDR might not have, to respond to threat actors leveraging Sliver.
Finally, we discussed the network protocols Sliver supports to communicate with targeted systems, the use of which can be detected by fingerprinting the TLS configurations of C2 servers. We explored other methods of detecting abnormal network traffic initiated by Sliver and finished with a discussion about the various detection possibilities.
Moving forward, at Hunt & Hackett we will continue to keep an eye on adversary emulation frameworks and the techniques that (advanced) threat actors use to achieve their objectives, to leverage this knowledge for our Managed Detection & Response (MDR) and Incident Response (IR) services.
References
- https://www.ncsc.gov.uk/files/Advisory%20Further%20TTPs%20associated%20with%20SVR%20cyber%20actors.pdf
-
https://www.microsoft.com/en-us/security/blog/2022/05/09/ransomware-as-a-service-understanding-the-cybercrime-gig-economy-and-how-to-protect-yourself/, https://blog.talosintelligence.com/avoslocker-new-arsenal/
- https://github.com/BishopFox/sliver
- https://www.proofpoint.com/us/blog/threat-insight/cobalt-strike-favorite-tool-apt-crimeware
- https://github.com/sliverarmory/armory/blob/master/armory.json
- https://kwcsec.gitbook.io/the-red-team-handbook/techniques/initial-access/staging-stagers
- https://attack.mitre.org/software/S0633/
- https://securityintelligence.com/articles/all-about-powershell-attacks/
- https://github.com/BishopFox/sliver/issues/1065
- https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
- https://github.com/SwiftOnSecurity/sysmon-config/blob/master/sysmonconfig-export.xml
- https://docs.velociraptor.app/blog/2021/2021-04-16-digging-into-process-memory-33c60a640cdb/
- https://github.com/salesforce/jarm
- https://attack.mitre.org/tactics/TA0011/
- https://www.shodan.io/search?query=product%3Asliver