Incident Response Retainer
Prepare, respond, recover, and learn from cybersecurity incidents.
The Incident Response Retainer ensures 24/7 access to our dedicated Computer Emergency Response Team (CERT), ready to investigate, contain, and resolve cybersecurity incidents.
With years of experience, we quickly assess the situation, stabilize your environment, mitigate immediate threats, and support crisis management. But we don’t stop at firefighting—when we’re not responding to incidents, we help you learn from them. By strengthening your in-house readiness and response capabilities, we enable you to handle cyber threats more effectively in the long run.
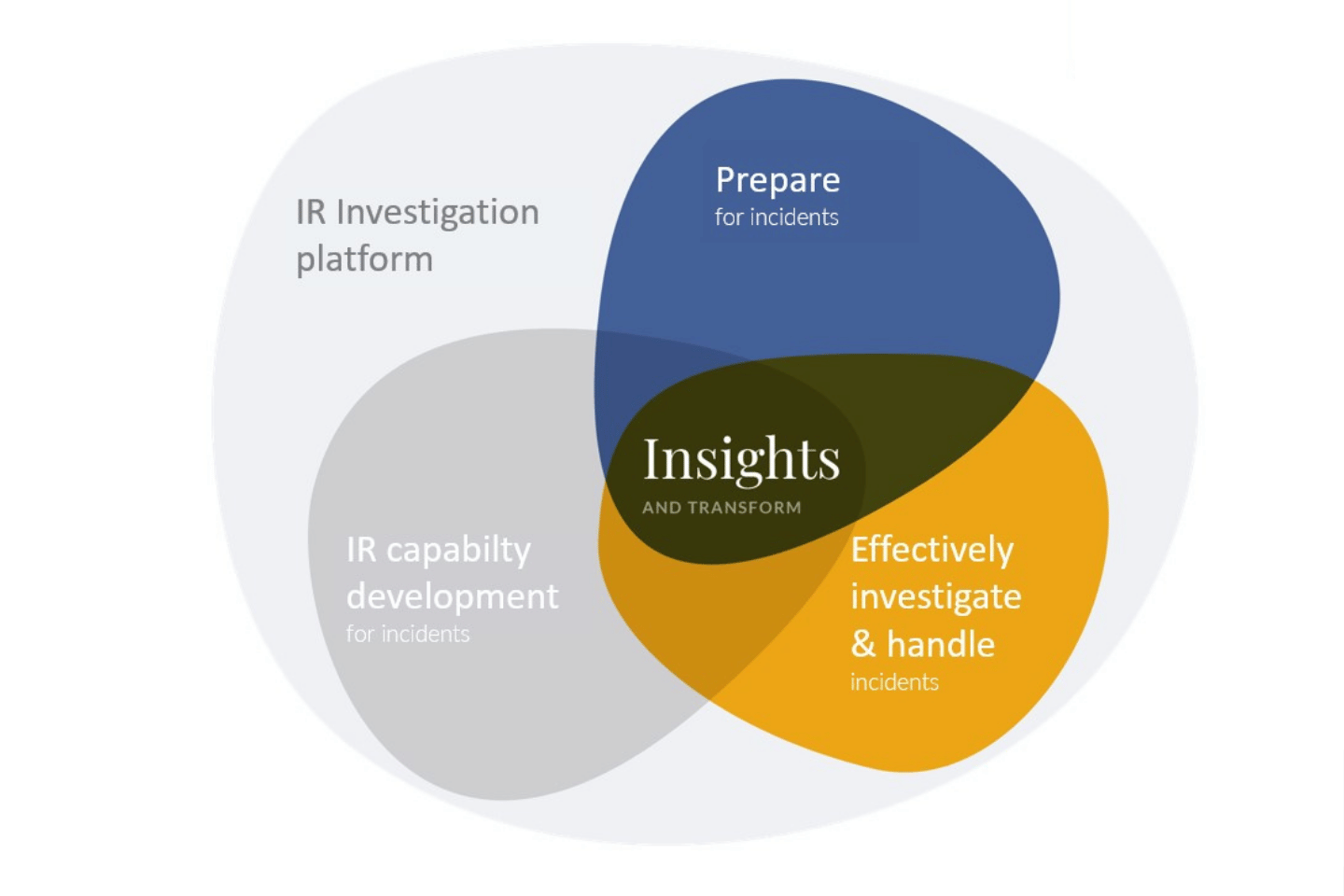
The Benefits
Prepare. Respond. Win.
24/7 guaranteed response & crisis mgmt
Proactive incident readiness
Rapid NIS2 notification readiness
Incident response capability development
The Challenge
when, not if
Cyber incidents are a question of when, not if. While organizations can take steps to manage cyber risks, no amount of preparation can fully prevent a determined attack. From disruptive ransomware incidents to Business Email Compromise and targeted espionage, the range of threats continues to evolve, and maintaining control of your security becomes increasingly difficult. And with the arrival of the NIS2 Directive, the need for a concrete, actionable incident response plan is now a requirement, not just a recommendation.
Ransomware
When ransomware strikes, swift and decisive action is required to isolate the malware, remove attackers, and secure your environment. One of the key advantages of the Retainer (beyond 24/7 expert availability) is the time saved on setup tasks — contract negotiations, briefings, and access provisioning are already taken care of, allowing us to start investigating immediately.
As your trusted security partner, we are already familiar with your company’s infrastructure and critical assets, enabling a faster, more precise response while minimizing the risk of errors.
Our incident response team rapidly processes and analyzes the situation, giving you clear guidance in each step of the Incident Response process and peace of mind in critical moments.
Espionage
Cyber espionage is a common, yet extremely complex threat. Espionage cases require a far more delicate and strategic approach than other cyber incidents, as every investigative step risks alerting the attacker and triggering a counter-response. Successfully removing the intruder demands a coordinated and comprehensive strategy to eliminate all access points without tipping them off.
This involves simultaneous actions, such as identifying and removing persistence mechanisms and isolating compromised systems to contain the threat.
Having experts guide this process is crucial. With our Incident Response Retainer, your organization has immediate access to seasoned incident handlers who can navigate the complexities of cyber espionage, safeguarding your critical assets, reputation, and long-term financial stability.
Business Email Compromise
At Hunt & Hackett, we have observed a discernible increase in Business Email Compromise (BEC) in recent years. These attacks typically involve cybercriminals gaining unauthorized access to internal email accounts, often through phishing, credential theft, or exploiting vulnerabilities. Once inside, attackers monitor communications, impersonate key personnel, and manipulate conversations to authorize fraudulent transactions, redirect payments, or extract sensitive information.
An Incident Response Retainer provides your organization with immediate access to our experts who specialize in responding to BEC incidents. Incident handlers can quickly identify compromised accounts, trace attacker activity, and secure your email environment to prevent further damage. They can also offer guidance to mitigate the risk of future BEC attacks, such as making changes to your organization's payment processes or implementing hardware-based authentication measures.
The NIS2 Directive
The NIS2 Directive mandates stricter cybersecurity measures for organizations in a range of sectors. To comply with these measures, organizations are implicitly expected to: 1) Be prepared to deal with cyber security incidents; and 2) Conduct efficient incident investigations.
Among the changes, incident reporting timelines are becoming significantly shorter than those laid out by the original NIS Directive. Organizations will now have to submit an early warning within 24 hours, a more detailed incident notification within 72 hours, and a final report, including a root cause analysis, within one month. These requirements implicitly necessitate on-demand incident response capabilities.
Organizations falling under the scope of NIS2 are also expected to increase their incident readiness. When searching for an incident response retainer, it is therefore necessary to find a partner who goes beyond the availability aspect, who will work with your company to improve in-house capabilities, create actionable incident response playbooks, and increase the maturity of your organization's cybersecurity strategy.Immediate support when you need it most
When a cyberattack happens, every moment counts; a retainer eliminates time lost in contracting or onboarding a new security partner, allowing the response to begin immediately. This is crucial for damage limitation, especially when dealing with incidents like ransomware, where delays can cause extended downtime, financial loss, and reputational damage.
But response is only one part of the equation. Our retainer also helps organizations strengthen their resilience to cyber threats by proactively improving their readiness. Through tabletop exercises, crisis simulations, and regular check-ins, companies can refine their response strategies and ensure their teams are prepared for real-world incidents.
With regulators increasingly mandating faster response times and evidence of preparedness, an Incident Response Retainer is a practical way to meet compliance requirements while proactively managing risk. By combining incident readiness with rapid response, businesses can minimize the impact of cybersecurity incidents and safeguard their operations, reputation, and long-term stability.
Your trusted partner
A selection of our innovative clients in various sectors




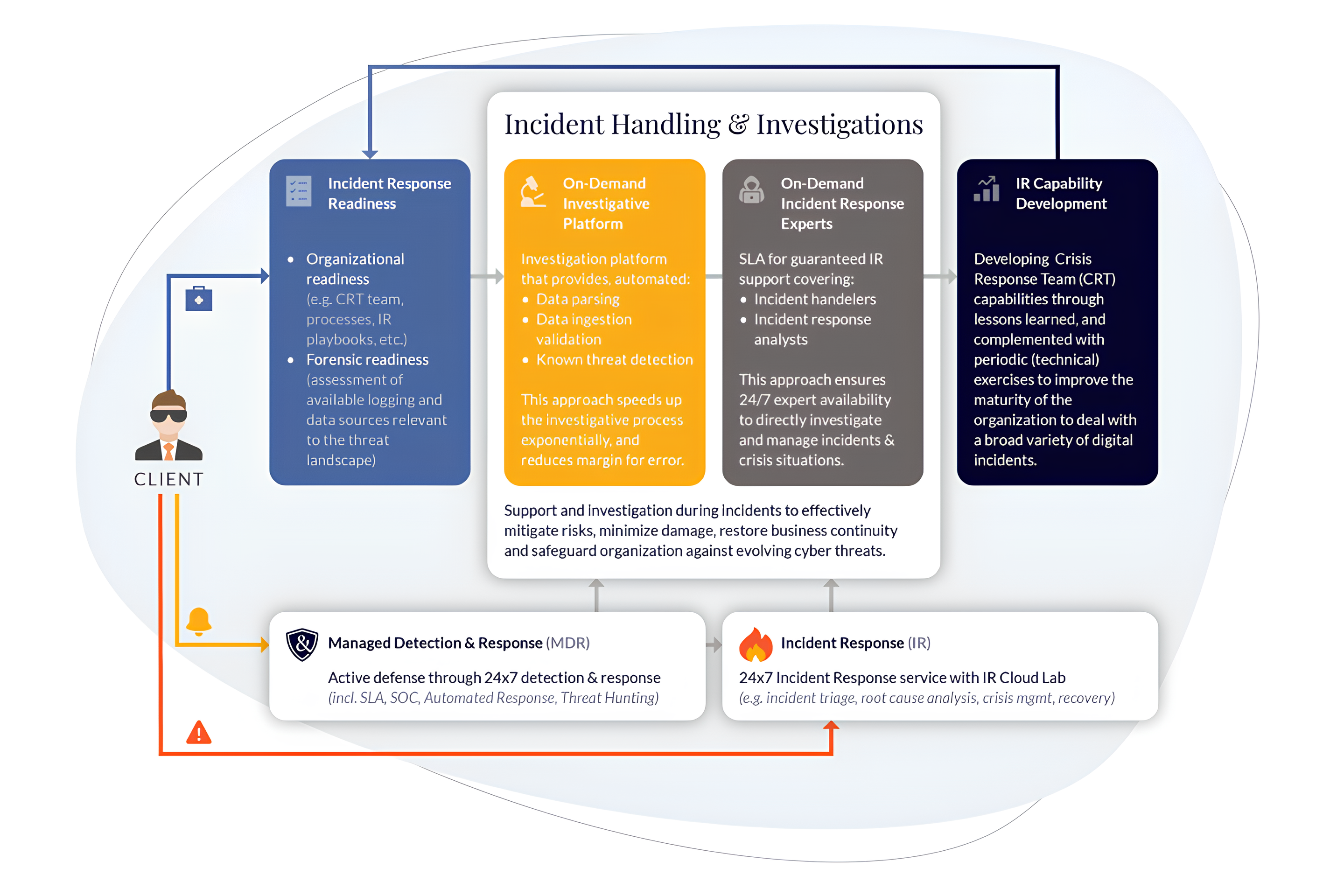
What you get
- Fast, scalable investigations
Our Incident Response Lab speeds up data collection and analysis during the early stages of the investigation, allowing us to identify compromised systems much faster than with traditional methods. - Low investigation threshold
Upload forensic data directly to the lab when suspicious activity occurs, so you can determine the necessity of further actions. Having these materials on-hand eliminates the start-up time of an investigation, improving forensic readiness. - Thorough forensic analysis
We strive to operate with the speed of an attacker and the depth of a forensic investigator. After resolving immediate issues, we perform a root cause analysis to find the source of the incident.
- Post-incident reporting
Our findings and analysis are compiled into a detailed incident report which can be tailored to meet your organization's requirements. - Enhanced incident readiness
We assess your current incident readiness and guide the creation of processes and procedures at both the organizational and technical level. This is done through tabletop exercises, workshops, incident playbooks, and consultation with Hunt & Hackett's experts. - IR capability development
We help you develop your in-house crisis management capabilities through lessons learned, complemented with periodic (technical) exercises to improve the maturity of your organization.
Why Hunt & Hackett?
Your trusted ally in cybersecurity
Frontline Experience
With more than 20 years of experience, our experts have a proven track record in dealing with high-profile cyber incidents such as DigiNotar, Shamoon, and Belgacom.
Technology & Tools
Our unique cloud-based IR platform enables fast, scalable, and cost-effective investigations with real-time threat visibility.
A Proactive Partnership
We don't just fight fires; we're a proactive security partner who'll help you increase your resilience in the long run.




FAQ
Frequently asked questions
What types of incidents does the retainer cover?
The Incident Response Retainer covers a wide range of cybersecurity incidents, from targeted phishing and Business Email Compromise (BEC) to high-impact threats such as ransomware, data breaches, and cyber espionage.
Are there guaranteed response times in the event of an incident?
Yes. Our Service Level Agreement (SLA) guarantees 24/7 access to our Incident Response experts.
Additionally, clients can start an investigation even before calling, by directly uploading forensic files to our cloud-based Incident Response Lab as soon as suspicious activity is detected. This allows our team to begin investigations immediately, significantly reducing response times compared to traditional security providers.
How is pricing determined, and are there any additional costs during an incident?
Pricing of the retainer is dependent on the package you will choose. The desired SLA defines response times, pre-paid hours, table-top exercises, and a Security Program Gap Assessment (SPGA) will determine the pricing, to name a few. Want to learn more about the pricing options? Give us a call!
Does Hunt & Hackett coordinate with external stakeholders such as insurers, legal teams, and law enforcement?
Hunt & Hackett’s experts manage multi-stakeholder coordination throughout the incident response process. This can include facilitating insurance claims, working with legal teams, filing police reports, and, when necessary, negotiating with attackers.
If I work with a different managed service provider, can I still retain Hunt & Hackett for incident response?
Yes. Your existing contract with a Managed Service Provider (MSP), such as an MDR provider, does not affect your ability to engage Hunt & Hackett for incident response. Our IR Retainer operates independently, and we have extensive experience collaborating with a wide range of technology partners during incident response cases to ensure a seamless and effective resolution.
Articles about Incident Response
from Hunt & Hackett experts
Get in touch
Let's outsmart your digital adversaries